The tool to browse the Internet anonymously
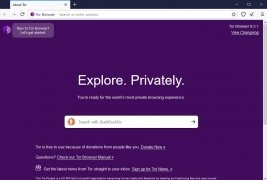
Tor has the solution to be able to solve your privacy problems: browse anonymously. If you don't like leaving a trail, you want to connect to networks you can't access or you need to avoid a proxy or similar protection, Tor Browser is a tool that will encrypt your browsing and make it impossible for anybody to follow your steps.
Everything you need to browse the Internet safely
Even though the encryption of the data that is sent and received isn't 100% secure, it has to be said that user's anonymity is assured. This software uses a technology called “onion routing” that uses a large structure of servers that are specialized in hiding the IP and all the user information. Tor has a design that is prepared to support high scale attacks that try to find out the identity of any of its users.
As it quotes on its own website, many journalists, NGOs and bloggers use Tor Browser to manage to avoid the censorship of the countries in which they work, because even if the data that is sent can be seen, it will be impossible to find out from where. Furthermore, it's also possible to create a web server that connects via Tor, thus assuring that its location is totally secure.
Safe browsing without censorship or restrictions.
This program turns out to be a really easy-to-use software application that connects automatically to the proper server and starts to work instantly without the user having to configure any parameters, but with the possibility to complete all kinds of configurations if needed and if you've got the knowledge necessary for such actions.
This browser has become tremendously popular over the last few years due to the growing psychosis about spying cases carried out by governmental organizations, with the NSA taking the top spot. In fact, not only can we download Tor for Windows PCs but there's also a version for Mac and Linux. In terms of mobile devices, both Android and iOS have browsers based on this same technology although they're not developed under the same project, offering us similar anonymity and privacy guarantees.
It has been developed based on the open-source version of Mozilla Firefox but, obviously, modifying the part of the code that makes Mozilla's official browser a vulnerable product in terms of privacy, just like Chrome or Opera.
Requirements and additional information:
- Minimum operating system requirements: Windows 7.
 Antony Peel
Antony Peel
A Telecommunications Engineer, chance led me to the translation industry, where after a few years, I discovered another side of the world of technology while translating what others were writing about mobile applications and software. That...